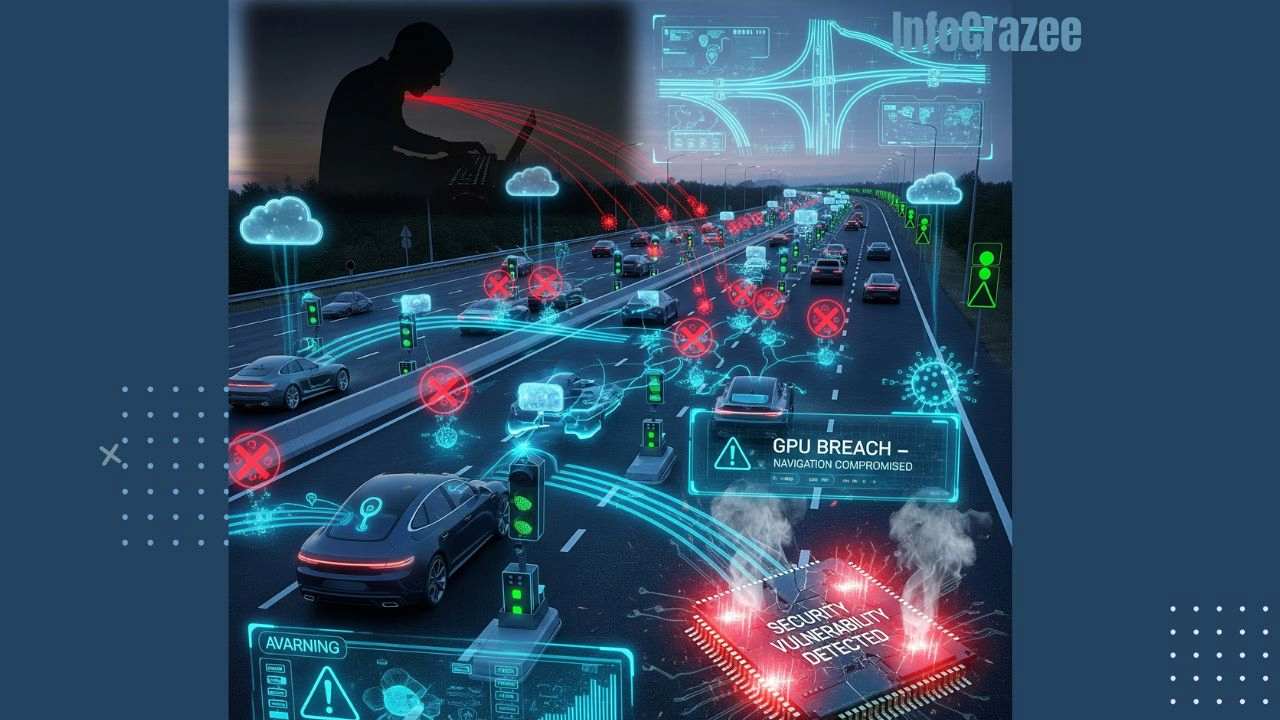
GPU Vulnerabilities Threaten Cybersecurity of Intelligent Transportation Systems and Autonomous Vehicles
As intelligent transportation systems (ITS) and autonomous vehicles (AVs) reshape mobility in 2025, their reliance on graphics processing units (GPUs) for high-performance computing introduces critical cybersecurity risks. GPUs, essential for tasks like sensor fusion, video analytics, and real-time decision-making, are increasingly targeted by sophisticated cyber attack, such as cryptojacking, that can compromise safety and reliability. Research from Clemson University, published in IEEE Transactions on Intelligent Transportation Systems on August 6, 2025, underscores GPUs as a significant blind spot in transportation cybersecurity. This blog explores these vulnerabilities, their implications for ITS and AVs, and strategies to strengthen defenses, ensuring the safety of next-generation transportation systems.
The Role of GPUs in ITS and AVs
GPUs are the computational backbone of ITS and AVs, enabling high-throughput, energy-efficient processing for:
- Sensor Fusion: Combining data from cameras, LiDAR, radar, and ultrasonic sensors to create a real-time 360-degree view of a vehicle’s environment.
- Video Analytics: Processing high-resolution video feeds for object detection, lane tracking, and traffic sign recognition.
- AI-Driven Decision-Making: Powering machine learning models that guide navigation, collision avoidance, and traffic optimization in AVs and roadside infrastructure.
With AVs expected to account for 15% of global vehicle sales by 2030, and ITS deployments growing in smart cities, GPUs are indispensable. However, their critical role makes them prime targets for cyberattacks, threatening both operational efficiency and passenger safety.
GPU Vulnerabilities: A Growing Threat
Research by Sefatun-Noor Puspa and Mashrur Chowdhury at Clemson University reveals that GPUs are highly vulnerable to stealthy attacks, particularly unauthorized cryptocurrency mining (cryptojacking). Key findings include:
- Performance Degradation: Malicious processes, such as cryptomining, can reduce GPU frame rates by up to 50% and increase power consumption by 90%, impairing critical functions like real-time video processing in AVs. For example, a case study showed a video processing pipeline’s performance halved under cryptojacking, potentially delaying obstacle detection.
- Stealthy Attacks: Unlike traditional CPU-based attacks, GPU exploits are harder to detect due to limited monitoring tools, allowing attackers to operate covertly.
- Attack Vectors: GPUs are susceptible to both software-based attacks (e.g., malicious code injected via unsecure APIs) and hardware vulnerabilities (e.g., side-channel attacks exploiting GPU memory).
These vulnerabilities extend beyond AVs to ITS infrastructure, such as smart traffic signals and vehicle-to-everything (V2X) communication systems, where compromised GPUs could disrupt traffic flow or falsify data.
Implications for ITS and AV Safety
The consequences of GPU vulnerabilities are severe, particularly in safety-critical systems:
- Compromised Perception Systems: Degraded GPU performance can slow sensor data processing, leading to delayed or inaccurate obstacle detection, increasing collision risks. For instance, a 50% frame rate drop could delay an AV’s reaction to a pedestrian by critical milliseconds.
- V2X Communication Risks: Compromised GPUs in roadside units could disrupt V2X protocols, sending false traffic data to vehicles and causing chaos in smart city networks.
- Public Trust and Adoption: High-profile incidents, like the 2024 Tesla OTA update addressing a remote hacking vulnerability, highlight how GPU-related breaches could erode confidence in AV technology, slowing adoption.
Current Challenges in GPU Security
Despite their critical role, GPUs remain one of the least monitored components in ITS and AVs:
- Lack of Observability: Unlike CPUs, GPUs lack robust telemetry for real-time monitoring, making it difficult to detect malicious activity early.
- Complex Attack Surfaces: The integration of GPUs with cloud services, in-vehicle networks (e.g., CAN bus), and external infrastructure (e.g., V2X) expands the attack surface, as noted in a 2024 ScienceDirect study on connected and automated vehicles (CAVs).
- Resource Constraints: Implementing security measures on resource-intensive GPUs without compromising performance is a significant challenge, particularly for real-time AV applications.
Strategies to Mitigate GPU Vulnerabilities
To address GPU vulnerabilities, a multi-layered cybersecurity approach is essential. Drawing from recent research and industry best practices, the following strategies can strengthen ITS and AV security:
1. Real-Time GPU Monitoring
- On-Device Telemetry: Implement lightweight monitoring software to track GPU performance metrics, such as frame rates and power consumption, as demonstrated in Clemson University’s replicable framework. This enables early detection of anomalies like cryptojacking.
- Anomaly Detection: Use AI-based intrusion detection systems (IDS) to identify abnormal GPU behavior, leveraging models like those proposed in a 2023 IEEE Transactions study on deep learning for AV security.
- Example: A 2025 pilot by an ITS provider used real-time GPU telemetry to detect a cryptomining attack on roadside video analytics, preventing a 30% performance drop.
2. Hardware-Level Security
- Secure GPU Architectures: Integrate hardware security modules (HSMs) to protect GPU memory from side-channel attacks, as recommended in a 2024 MDPI study on AV cybersecurity.
- Trusted Execution Environments: Use secure enclaves to isolate critical GPU processes, ensuring malicious code cannot access sensitive data.
3. Software-Based Defenses
- Secure APIs: Harden APIs used for GPU communication to prevent injection attacks, a common entry point for cryptojacking.
- Over-the-Air Updates: Implement secure OTA update systems, like Tesla’s, to deliver rapid patches for GPU vulnerabilities, minimizing the window for exploitation.
4. Collaborative Threat Intelligence
- Industry-Wide Standards: Develop standardized GPU security protocols, as advocated in a 2024 ScienceDirect study, to ensure consistent protection across AV and ITS manufacturers.
- Information Sharing: Foster collaboration among OEMs, cybersecurity firms, and regulators to share threat intelligence, enabling proactive defenses against emerging GPU exploits.
5. User and OEM Education
- Cybersecurity Awareness: Train ITS operators and AV developers on GPU-specific threats, such as cryptojacking, to improve proactive monitoring and response.
- Public Awareness: Educate consumers about AV cybersecurity risks to maintain trust, as highlighted in a 2023 MDPI study on AV adoption.
The Path Forward
As ITS and AVs evolve, addressing GPU vulnerabilities will be critical to ensuring safety and reliability. By 2030, with AVs projected to dominate urban mobility, robust GPU security will be non-negotiable. Ongoing research, such as Clemson University’s work, emphasizes the need for:
- Advanced Detection Tools: Developing AI-driven IDS tailored for GPU telemetry to counter sophisticated attacks.
- Regulatory Frameworks: Enforcing cybersecurity standards for GPU integration in AVs and ITS, as proposed in a 2024 ScienceDirect study on CAV risk classification.
- Investment in R&D: Funding collaborative initiatives to innovate GPU security solutions, including blockchain and generative AI, as explored in a 2025 ScienceDirect study on LLM-powered threat intelligence.
Conclusion
GPU vulnerabilities represent a critical cybersecurity blind spot in intelligent transportation systems and autonomous vehicles, threatening performance, safety, and public trust. By implementing real-time monitoring, hardware and software defenses, and collaborative threat intelligence, stakeholders can mitigate these risks. For ITS operators, AV manufacturers, and policymakers, prioritizing GPU security is essential to unlocking the full potential of next-generation transportation while safeguarding lives and infrastructure. As the industry races toward a connected, autonomous future, proactive measures today will ensure a secure and resilient tomorrow.