Vietnamese-Speaking Hackers Suspected of Running Global Data Theft Operation via Telegram
A sophisticated cyber crimes campaign orchestrated by Vietnamese-speaking hackers has compromised sensitive data from thousands of victims across 62 countries, leveraging Telegram bots to automate the theft and resale of information, according to a joint report by Beazley Security Labs and Sentinel Labs released on August 5, 2025. The operation, driven by a Python-based malware called PXA Stealer, highlights the growing abuse of legitimate platforms like Telegram for large-scale cyber criminals activities.
A Highly Evasive Operation
The campaign, which has infected over 4,000 unique IP addresses, uses phishing lures disguised as legitimate software, such as Microsoft Word 2013 or Haihaisoft PDF Reader, to deliver PXA Stealer. In a July 2025 wave, attackers deployed a signed Microsoft Word executable posing as a copyright infringement notice, evading detection by avoiding malicious links. Once installed, the malware harvests passwords, financial credentials, browser cookies, and cryptocurrency wallet data, compressing it into ZIP files and exfiltrating it via Cloudflare Workers to Telegram bot channels, such as one linked to a central account, @Lonenone, featuring a Vietnam flag emoji.
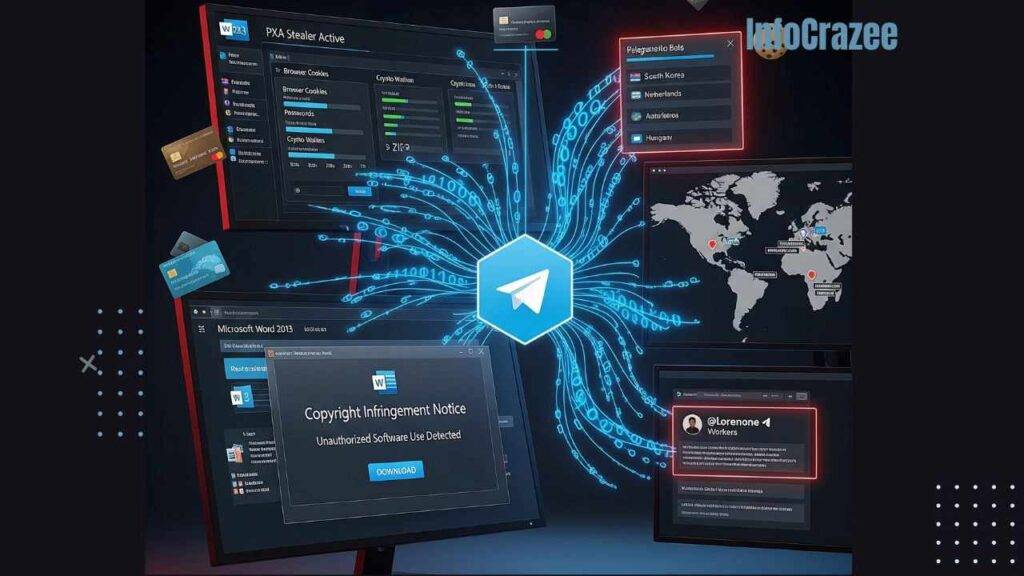
The operation’s scale is staggering, with over 200,000 unique passwords and 4 million browser cookies stolen, alongside hundreds of credit card records. Victims span the United States, South Korea, the Netherlands, Austria, Hungary, and beyond, with a focus on government and educational institutions. The malware’s advanced evasion techniques, including DLL side-loading and decoy documents, make it a formidable threat, according to researchers Jim Walter and Alex Delamotte.
Telegram as a Cybercrime Hub
The hackers monetize their haul through Telegram-based subscription services like Sherlock, Daisy Cloud, and Moon Cloud, which automate the resale of stolen data to other criminals for financial fraud, cryptocurrency theft, or organizational breaches. “The developer-friendly nature of Telegram, combined with its lax approach to cybercrime, makes it a linchpin in the infostealer ecosystem,” the report notes. Vietnamese-language Telegram bots and channels, some linked to the Coral Raider group, streamline this underground marketplace, with tools like Hotmail batch creation and email mining software shared openly.
This isn’t the first time Vietnamese-speaking hackers have exploited Telegram. A November 2024 Cisco Talos report identified PXA Stealer targeting Facebook ad accounts and credentials, with connections to a Telegram channel, “Mua Bán Scan MINI,” suggesting ties to organized cybercrime networks. While it’s unclear if the current campaign directly involves Coral Raider, the use of Vietnamese comments and hard-coded Telegram accounts like “Lone None” points to a consistent threat actor profile.
Global Impact and Response
The campaign’s indiscriminate targeting affects both individual users and corporations, fueling downstream crimes like ransomware and data breaches. Cloudflare, upon being notified, disrupted the attackers’ use of its Workers service, but the operation’s resilience underscores the challenge of combating Telegram-based cybercrime. Vietnam’s own struggles with Telegram scams, including a 2024 case in Ba Ria-Vung Tau where hackers defrauded 100 victims of $1.42 million via 10,000 chat groups, highlight the platform’s role as a haven for cybercriminals.
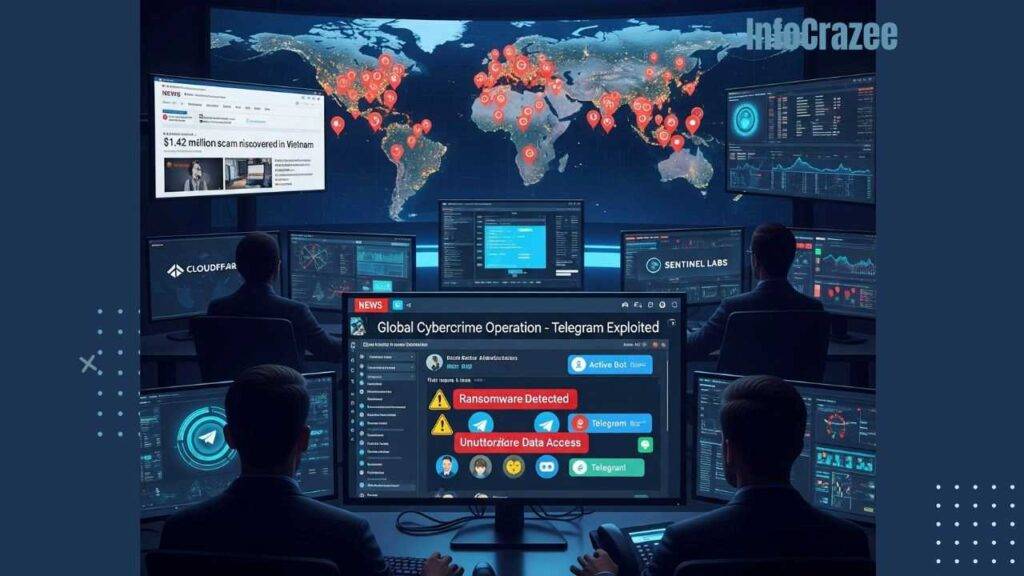
Authorities and cybersecurity experts are urging stronger defenses. Recommendations include monitoring Telegram bot traffic, deploying endpoint detection and response (EDR) systems to catch anomalies, and enabling multi-factor authentication (MFA) for critical accounts. “Organizations must prioritize user training and network monitoring to counter these sophisticated threats,” said Sentinel Labs researcher Sam Mayers.
A Wake-Up Call
The PXA Stealer campaign reflects a broader trend of cybercriminals weaponizing legitimate platforms for profit. With Telegram’s user base in Vietnam exceeding 31.5% of internet users aged 16-64, and its global reach growing, the platform’s role in cybercrime is under scrutiny. As Vietnam pushes for stricter data protection under Decree No.13/2023/ND-CP, the global community faces the challenge of balancing platform accessibility with robust security measures to curb operations like this one.